Hirdetés
- AMD Ryzen 9 / 7 / 5 7***(X) "Zen 4" (AM5)
- SONY LCD és LED TV-k
- Fejhallgató erősítő és DAC topik
- Apple notebookok
- Érezhetően gyorsít az új Ryzeneken az érkező Windows frissítés
- Milyen TV-t vegyek?
- Ajánlatott tett a Qualcomm az Intelért?
- HiFi műszaki szemmel - sztereó hangrendszerek
- Vezetékes FEJhallgatók
- Azonnali VGA-s kérdések órája
Hirdetés
-
"A homoszexualitás természetellenes" 😠
lo Ehhez képest a természetben nem ritka és evolúciós előnyei is vannak. ...
-


Shadows of Doubt teszt
gp Vajon mennyire – és meddig – lehet szórakoztató egy véletlenszerűen generált detektíves játék? Végtelen mélységű összeesküvések várnak vagy csak felületes ügyek? Kinyomoztuk, mit is kínál ez az ambiciózus indie projekt!
-


A Pwnage kínálatában hamarosan megjelenik az eddigi legkönnyebb nagy méretű egér
ph A Razer DeathAdder V3-ból merítő, szénszálas megoldás sok színben választható, a szenzora áthelyezhető, és még 45 gramm sincs.
-

PROHARDVER!
Vírusirtó Topic 2019
Új hozzászólás Aktív témák
-

ƵøŁĭ
veterán
The download link of the VSDC video editor software on the CNET’s Downloads webpage has been compromised by malicious actors, resulting in the downloading of thousands of infected installers. The hackers have set up a spoofed domain on “downloads[.]videosfotdev[.]com”, which contains the installer of the video editing software, but is also bundled with a trojan.
The discovery was made by the Dr. Web Antivirus team of researchers, and the malicious file is identified as “BackDoor.TeamViewer”. A script in the trojan enables the file to bypass the Microsoft Windows Defender protection and to establish communication with the C2 server.
From there, additional payloads and modules are fetched. The researchers have noticed an X-Key Keylogger, Predator The Thief stealer, SystemBC trojan-proxy, and a trojan for remote control over RDP protocol.Those who have been following the news section here, you may remember that this is not the first time that VSDC becomes the target of malicious actors. Back on April 12, 2019, the same team of researchers discovered that hackers had replaced the original installer of the video editor with banking trojans.
VSDC hack — Indicators of compromise
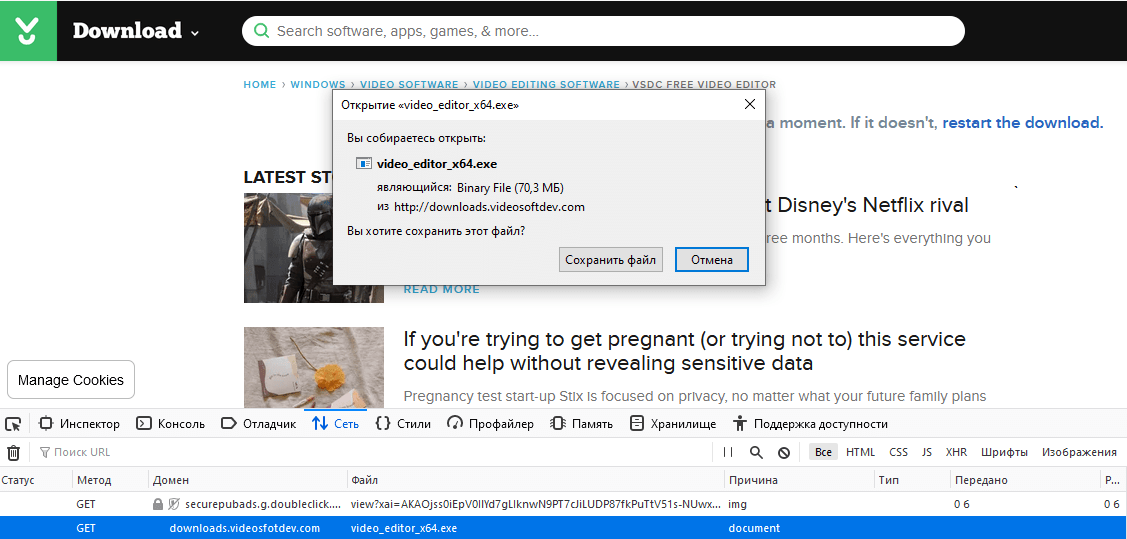
[ Szerkesztve ]
(ง'̀-'́)ง(ง'̀-'́)ง
Új hozzászólás Aktív témák
● TILOS a warez!
● Vírusos, vagy egyéb kártevőt tartalmazó linkek a topikban való elhelyezésére vonatkozó szabály:
Tilos a topikban bármilyen vírusos vagy lehetséges vírusos kártevő link elhelyezése.
Az ilyen linkek megosztása csak privátban, PH tagok számára osztható meg.
Ellenkező esetben a hozzászólás törölve lesz.
- Tőzsde és gazdaság
- Ford topik
- Telekom otthoni szolgáltatások (TV, internet, telefon)
- Xiaomi 13T és 13T Pro - nincs tétlenkedés
- Öt Starship után embereket küldene a Marsra Musk és a SpaceX
- AMD Ryzen 9 / 7 / 5 7***(X) "Zen 4" (AM5)
- Kínai és egyéb olcsó órák topikja
- Android szakmai topik
- World of Tanks - MMO
- Samsung Galaxy S23 és S23+ - ami belül van, az számít igazán
- További aktív témák...
- World of Warcraft (WoW) Díszdobozok
- Call of Duty Mwii Ghost kézzel készített maszk + ingyen foxpost
- Bontatlan - BATTLEFIELD 1 Collectors Edition - Játékszoftver nélkül
- Vírusirtó, Antivirus, VPN kulcsok
- Microsoft licencek KIVÉTELES ÁRON AZONNAL - UTALÁSSAL IS AUTOMATIKUS KÉZBESÍTÉS - Windows és Office
Állásajánlatok
Cég: Ozeki Kft
Város: Debrecen
Cég: Ozeki Kft
Város: Debrecen






 Szellem.
Szellem.

