Hirdetés
-


Kevés esélye van a hangalapú közösségi médiának
it A hangközpontú AirChat célja, hogy lenyomja az X-et és a Meta Threadset – a hasonló próbálkozások alapján azonban elég kevése az esélye erre.
-


Megérkezett Európába a Nubia Z60 Ultra Photographer Edition
ma Elindult a Nubia fotós csúcsmobiljának nemzetközi értékesítése, egyedi hátlappal is beszerezhető a Z60 Ultra.
-


Lenovo Essential Wireless Combo
lo Lehet-e egy billentyűzet karcsú, elegáns és különleges? A Lenovo bebizonyította, hogy igen, de bosszantó is :)
-

PROHARDVER!
Ebben a témában VPN-el kapcsolatos kérdéseket lehet megbeszélni, különféle VPN szolgáltatók, és VPN képes eszközök, pl. VPN-t is tudó routereken, NAS-okon a VPN használata. Különféle VPN típusok (PPTP, L2TP, OVPN, WG, SSTP, stb...), pl. melyiket érdemes, mik a különbségek, előnyök-hátrányok.
Új hozzászólás Aktív témák
-

btz
addikt
HELP: DHCP és StrongSwan IPSEC Ikev2 ugyanazon a szerveren nem megy(?)
Sajnos arra lettem figyelmes, hogy a már jó egy éve bejáratott VPN-em nem működik, pedig semmilyen változtatást nem hajtottam végre a konfigurációban.
A VPN szerver még mindig az Openwrt-s TP-Link, a gateway még mindig a Telekomos Speedport Entry 2i.
A valahogy így néz ki a hálózat: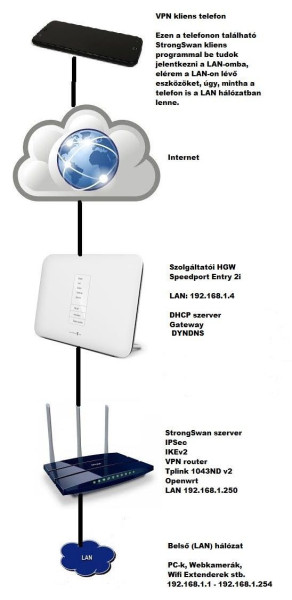
Mit változtattam?
A Speedport helyett a TP-Link lett a DHCP szerver. Ha visszaállítom a Speedportot DHCP szervernek, minden működik, a VPN kliens tud csatlakozni a szerverhez, IP címet is kap a DHCP szerver Speedport által, Ha ismét a TP-Linket állítom be DHCP szervernek, akkor nem működik az egész. Pedig a helyi hálózaton keresztül csatlakoztatott eszközök kapnak IP-t a TP-Linktől, Internet is van, mivel a TP-Link DHCP szervere Gateway-nek az Speedport IP-jét (ami 192.168.1.4) adja a klienseknek nem a sajátját az 192.168.1.250-et.Az IPsec jelenlegi konfigurációs fájljában az ipsec.conf-ban, ez van:
config setup
charondebug="ike 2, knl 2, cfg 2, net 2, esp 2, dmn 2, mgr 2"
#uniqueids=never
charondebug="cfg 2, dmn 2, ike 2, net 2"
conn %default
# Dead Peer Discovery
dpdaction=clear
dpddelay=300s
# Do not renegotiate a connection
#if it is about to expire
rekey=no
conn BASE
#Left server side
left=%any
leftfirewall=yes
leftcert=btzSERVER_CERT.pem
leftsubnet=0.0.0.0/0,::/0
#Right client side
#rightsendcert=never
right=%any
rightdns=8.8.8.8,8.8.4.4
rightsourceip=%dhcp #EZZEL A DHCPVEL LEHET CÍMET KAMPNI, EZZEL NEM MŰKÖDIK
#rightsourceip=192.168.1.90-192.168.1.96 #EZZEL MŰKÖDIK AKKOR IS HA A TPLINK A DHCP SZERVER
keyexchange=ikev2
auto=add
conn EAP0
also="BASE"
leftsendcert=always
#leftid=@btzdomainje.com
rightauth=eap-mschapv2
rightsendcert=never
eap_identity=%any
conn EAP1
also="BASE"
leftauth=pubkey
leftsendcert=always
rightauth=pubkey
rightauth2=eap-md5
eap_identity=%anyrightsourceip=%dhcp esetén csak akkor kap címet a VPN kliens, ha a Speedport a szerver.
rightsourceip=192.168.1.90-192.168.1.96 esetén kap címet a beállított tartományból 90 és 96 között.Egyik fórum javaslatára a /etc/strongswan.d/charon/dhcp.conf fájlt az alábbiak szerint állítottam be:
dhcp {
# Always use the configured server address.
force_server_address = yes
# Derive user-defined MAC address from hash of IKE identity.
identity_lease = yes
# Interface name the plugin uses for address allocation.
interface = lan
# Whether to load the plugin. Can also be an integer to increase the
# priority of this plugin.
load = yes
# DHCP server unicast or broadcast IP address.
server = 192.168.1.255
}
Sajnos ezzel nem oldódott meg a probléma. A VPN kliens nem tud csatlakozni, továbbra sem.ipsec statusall parancs kimenete
Status of IKE charon daemon (strongSwan 5.3.3, Linux 3.18.23, mips):
uptime: 6 minutes, since May 27 12:42:57 2018
malloc: sbrk 249856, mmap 0, used 246208, free 3648
worker threads: 9 of 16 idle, 7/0/0/0 working, job queue: 0/0/0/0, scheduled: 0
loaded plugins: charon test-vectors ldap pkcs11 aes des blowfish rc2 sha1 sha2 md4 md5 random nonce x509 revocation constraints pubkey pkcs1 pkcs7 pkcs8 pkcs12 pgp dnskey sshkey pem openssl gcrypt af-alg fips-prf gmp agent xcbc cmac hmac ctr ccm gcm curl mysql sqlite attr kernel-netlink resolve socket-default farp stroke smp updown eap-identity eap-md5 eap-mschapv2 eap-radius eap-tls xauth-generic xauth-eap whitelist led duplicheck uci addrblock unity
Listening IP addresses:
192.168.1.250
2001:(PRIVÁT ADAT)::1
2001:(PRIVÁT ADAT)::2
Connections:
BASE: %any...%any IKEv2, dpddelay=300s
BASE: local: [C=CA, O=btzdomainje.com, CN=btzdomainje.com] uses public key authentication
BASE: cert: "C=CA, O=btzdomainje.com, CN=btzdomainje.com"
BASE: remote: uses public key authentication
BASE: child: 0.0.0.0/0 ::/0 === dynamic TUNNEL, dpdaction=clear
EAP0: %any...%any IKEv2, dpddelay=300s
EAP0: local: [C=CA, O=btzdomainje.com, CN=btzdomainje.com] uses public key authentication
EAP0: cert: "C=CA, O=btzdomainje.com, CN=btzdomainje.com"
EAP0: remote: uses EAP_MSCHAPV2 authentication with EAP identity '%any'
EAP0: child: 0.0.0.0/0 ::/0 === dynamic TUNNEL, dpdaction=clear
EAP1: %any...%any IKEv2, dpddelay=300s
EAP1: local: [C=CA, O=btzdomainje.com, CN=btzdomainje.com] uses public key authentication
EAP1: cert: "C=CA, O=btzdomainje.com, CN=btzdomainje.com"
EAP1: remote: uses public key authentication
EAP1: remote: uses EAP_MD5 authentication with EAP identity '%any'
EAP1: child: 0.0.0.0/0 ::/0 === dynamic TUNNEL, dpdaction=clear
Security Associations (0 up, 0 connecting):
noneA kliensen ez található a logban:
May 27 12:55:29 00[DMN] Starting IKE charon daemon (strongSwan 5.6.1dr3, Android 7.0 - KOB-L09C100B252/2017-11-06, KOB-L09 - HUAWEI/KOB/HUAWEI, Linux 3.18.31-gd04fcee, aarch64)
May 27 12:55:29 00[LIB] loaded plugins: androidbridge charon android-log openssl fips-prf random nonce pubkey chapoly curve25519 pkcs1 pkcs8 pem xcbc hmac socket-default revocation eap-identity eap-mschapv2 eap-md5 eap-gtc eap-tls x509
May 27 12:55:29 00[JOB] spawning 16 worker threads
May 27 12:55:30 07[CFG] loaded user certificate 'C=CA, O=btzdomainje.com, CN=CLIENT@btzdomainje.com' and private key
May 27 12:55:30 07[CFG] loaded CA certificate 'C=CA, O=btzdomainje.com, CN=btzdomainje.com Root btzCA'
May 27 12:55:30 07[IKE] initiating IKE_SA android[1] to 78.XXX.XXX.XXX (Privát adat)
May 27 12:55:30 07[ENC] generating IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(REDIR_SUP) ]
May 27 12:55:30 07[NET] sending packet: from 192.168.1.232[42519] to 78.XXX.XXX.XXX (Privát adat)[500] (704 bytes)
May 27 12:55:30 10[NET] received packet: from 78.XXX.XXX.XXX (Privát adat)[500] to 192.168.1.232[42519] (38 bytes)
May 27 12:55:30 10[ENC] parsed IKE_SA_INIT response 0 [ N(INVAL_KE) ]
May 27 12:55:30 10[IKE] peer didn't accept DH group ECP_256, it requested MODP_2048
May 27 12:55:30 10[IKE] initiating IKE_SA android[1] to 78.XXX.XXX.XXX (Privát adat)
May 27 12:55:30 10[ENC] generating IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(REDIR_SUP) ]
May 27 12:55:30 10[NET] sending packet: from 192.168.1.232[42519] to 78.XXX.XXX.XXX (Privát adat)[500] (896 bytes)
May 27 12:55:31 11[NET] received packet: from 78.XXX.XXX.XXX (Privát adat)[500] to 192.168.1.232[42519] (481 bytes)
May 27 12:55:31 11[ENC] parsed IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) CERTREQ N(HASH_ALG) N(MULT_AUTH) ]
May 27 12:55:31 11[IKE] local host is behind NAT, sending keep alives
May 27 12:55:31 11[IKE] remote host is behind NAT
May 27 12:55:31 11[IKE] received cert request for "C=CA, O=btzdomainje.com, CN=btzdomainje.com Root btzCA"
May 27 12:55:31 11[IKE] sending cert request for "C=CA, O=btzdomainje.com, CN=btzdomainje.com Root btzCA"
May 27 12:55:31 11[IKE] authentication of 'C=CA, O=btzdomainje.com, CN=CLIENT@btzdomainje.com' (myself) with RSA_EMSA_PKCS1_SHA2_256 successful
May 27 12:55:31 11[IKE] sending end entity cert "C=CA, O=btzdomainje.com, CN=CLIENT@btzdomainje.com"
May 27 12:55:31 11[IKE] establishing CHILD_SA android{1}
May 27 12:55:31 11[ENC] generating IKE_AUTH request 1 [ IDi CERT N(INIT_CONTACT) CERTREQ AUTH CPRQ(ADDR ADDR6 DNS DNS6) N(ESP_TFC_PAD_N) SA TSi TSr N(MOBIKE_SUP) N(NO_ADD_ADDR) N(MULT_AUTH) N(EAP_ONLY) N(MSG_ID_SYN_SUP) N(AUTH_FOLLOWS) ]
May 27 12:55:31 11[NET] sending packet: from 192.168.1.232[33004] to 78.XXX.XXX.XXX (Privát adat)[4500] (2044 bytes)
May 27 12:55:31 12[NET] received packet: from 78.XXX.XXX.XXX (Privát adat)[4500] to 192.168.1.232[33004] (1580 bytes)
May 27 12:55:31 12[ENC] parsed IKE_AUTH response 1 [ IDr CERT AUTH ]
May 27 12:55:31 12[IKE] received end entity cert "C=CA, O=btzdomainje.com, CN=btzdomainje.com"
May 27 12:55:31 12[CFG] using certificate "C=CA, O=btzdomainje.com, CN=btzdomainje.com"
May 27 12:55:31 12[CFG] using trusted ca certificate "C=CA, O=btzdomainje.com, CN=btzdomainje.com Root btzCA"
May 27 12:55:31 12[CFG] checking certificate status of "C=CA, O=btzdomainje.com, CN=btzdomainje.com"
May 27 12:55:31 12[CFG] certificate status is not available
May 27 12:55:31 12[CFG] reached self-signed root ca with a path length of 0
May 27 12:55:31 12[IKE] authentication of 'C=CA, O=btzdomainje.com, CN=btzdomainje.com' with RSA_EMSA_PKCS1_SHA2_256 successful
May 27 12:55:31 12[ENC] generating IKE_AUTH request 2 [ IDi ]
May 27 12:55:31 12[NET] sending packet: from 192.168.1.232[33004] to 78.XXX.XXX.XXX (Privát adat)[4500] (76 bytes)
May 27 12:55:31 13[NET] received packet: from 78.XXX.XXX.XXX (Privát adat)[4500] to 192.168.1.232[33004] (76 bytes)
May 27 12:55:31 13[ENC] parsed IKE_AUTH response 2 [ EAP/REQ/ID ]
May 27 12:55:31 13[IKE] server requested EAP_IDENTITY (id 0x00), sending 'btz'
May 27 12:55:31 13[ENC] generating IKE_AUTH request 3 [ EAP/RES/ID ]
May 27 12:55:31 13[NET] sending packet: from 192.168.1.232[33004] to 78.XXX.XXX.XXX (Privát adat)[4500] (76 bytes)
May 27 12:55:31 14[NET] received packet: from 78.XXX.XXX.XXX (Privát adat)[4500] to 192.168.1.232[33004] (92 bytes)
May 27 12:55:31 14[ENC] parsed IKE_AUTH response 3 [ EAP/REQ/MD5 ]
May 27 12:55:31 14[IKE] server requested EAP_MD5 authentication (id 0xCA)
May 27 12:55:31 14[ENC] generating IKE_AUTH request 4 [ EAP/RES/MD5 ]
May 27 12:55:31 14[NET] sending packet: from 192.168.1.232[33004] to 78.XXX.XXX.XXX (Privát adat)[4500] (92 bytes)
May 27 12:55:31 15[NET] received packet: from 78.XXX.XXX.XXX (Privát adat)[4500] to 192.168.1.232[33004] (76 bytes)
May 27 12:55:31 15[ENC] parsed IKE_AUTH response 4 [ EAP/SUCC ]
May 27 12:55:31 15[IKE] EAP method EAP_MD5 succeeded, no MSK established
May 27 12:55:31 15[IKE] authentication of 'btz' (myself) with EAP
May 27 12:55:31 15[ENC] generating IKE_AUTH request 5 [ AUTH ]
May 27 12:55:31 15[NET] sending packet: from 192.168.1.232[33004] to 78.XXX.XXX.XXX (Privát adat)[4500] (92 bytes)
May 27 12:55:31 16[NET] received packet: from 78.XXX.XXX.XXX (Privát adat)[4500] to 192.168.1.232[33004] (156 bytes)
May 27 12:55:31 16[ENC] parsed IKE_AUTH response 5 [ AUTH N(MOBIKE_SUP) N(ADD_6_ADDR) N(ADD_6_ADDR) N(INT_ADDR_FAIL) ]
May 27 12:55:31 16[IKE] authentication of 'C=CA, O=btzdomainje.com, CN=btzdomainje.com' with EAP successful
May 27 12:55:31 16[IKE] IKE_SA android[1] established between 192.168.1.232[btz]...78.XXX.XXX.XXX (Privát adat)[C=CA, O=btzdomainje.com, CN=btzdomainje.com]
May 27 12:55:31 16[IKE] scheduling rekeying in 35754s
May 27 12:55:31 16[IKE] maximum IKE_SA lifetime 36354s
May 27 12:55:31 16[IKE] received INTERNAL_ADDRESS_FAILURE notify, no CHILD_SA built
May 27 12:55:31 16[IKE] closing IKE_SA due CHILD_SA setup failure
May 27 12:55:31 16[IKE] peer supports MOBIKE
May 27 12:55:31 09[IKE] deleting IKE_SA android[1] between 192.168.1.232[btz]...78.XXX.XXX.XXX (Privát adat)[C=CA, O=btzdomainje.com, CN=btzdomainje.com]
May 27 12:55:31 09[IKE] sending DELETE for IKE_SA android[1]
May 27 12:55:31 09[ENC] generating INFORMATIONAL request 6 [ D ]
May 27 12:55:31 09[NET] sending packet: from 192.168.1.232[33004] to 78.XXX.XXX.XXX (Privát adat)[4500] (76 bytes)
May 27 12:55:31 08[NET] received packet: from 78.XXX.XXX.XXX (Privát adat)[4500] to 192.168.1.232[33004] (76 bytes)
May 27 12:55:31 08[ENC] parsed INFORMATIONAL response 6 [ ]
May 27 12:55:31 08[IKE] IKE_SA deletedA szerver logban pedig ez:
20180527124254 00[DMN] signal of type SIGINT received. Shutting down
20180527124257 00[DMN] Starting IKE charon daemon (strongSwan 5.3.3, Linux 3.18.23, mips)
20180527124257 00[LIB] curl SSL backend 'PolarSSL/1.3.14' not supported, https:// disabled
20180527124257 00[CFG] disabling load-tester plugin, not configured
20180527124257 00[LIB] plugin 'load-tester': failed to load - load_tester_plugin_create returned NULL
20180527124257 00[CFG] attr-sql plugin: database URI not set
20180527124257 00[CFG] loading ca certificates from '/etc/ipsec.d/cacerts'
20180527124257 00[CFG] loaded ca certificate "C=CA, O=btzdomainje.com, CN=btzdomainje.com Root btzCA" from '/etc/ipsec.d/cacerts/btzCA_CERT.pem'
20180527124257 00[CFG] loading aa certificates from '/etc/ipsec.d/aacerts'
20180527124257 00[CFG] loading ocsp signer certificates from '/etc/ipsec.d/ocspcerts'
20180527124257 00[CFG] loading attribute certificates from '/etc/ipsec.d/acerts'
20180527124257 00[CFG] loading crls from '/etc/ipsec.d/crls'
20180527124257 00[CFG] loading secrets from '/etc/ipsec.secrets'
20180527124257 00[CFG] loaded RSA private key from '/etc/ipsec.d/private/btzSERVER_KEY.pem'
20180527124258 00[CFG] loaded RSA private key from '/etc/ipsec.d/private/btzCLIENT_KEY.pem'
20180527124258 00[CFG] loaded EAP secret for btz
20180527124258 00[CFG] sql plugin: database URI not set
20180527124258 00[CFG] loaded 0 RADIUS server configurations
20180527124258 00[CFG] binding DHCP socket to 'lan' failed: No such device
20180527124258 00[CFG] HA config misses local/remote address
20180527124258 00[CFG] coupling file path unspecified
20180527124258 00[LIB] loaded plugins: charon test-vectors ldap pkcs11 aes des blowfish rc2 sha1 sha2 md4 md5 random nonce x509 revocation constraints pubkey pkcs1 pkcs7 pkcs8 pkcs12 pgp dnskey sshkey pem openssl gcrypt af-alg fips-prf gmp agent xcbc cmac hmac ctr ccm gcm curl mysql sqlite attr kernel-netlink resolve socket-default farp stroke smp updown eap-identity eap-md5 eap-mschapv2 eap-radius eap-tls xauth-generic xauth-eap whitelist led duplicheck uci addrblock unity
20180527124258 00[JOB] spawning 16 worker threads
20180527124258 10[CFG] received stroke: add connection 'BASE'
20180527124258 10[CFG] loaded certificate "C=CA, O=btzdomainje.com, CN=btzdomainje.com" from 'btzSERVER_CERT.pem'
20180527124258 10[CFG] id '%any' not confirmed by certificate, defaulting to 'C=CA, O=btzdomainje.com, CN=btzdomainje.com'
20180527124258 10[CFG] added configuration 'BASE'
20180527124258 11[CFG] received stroke: add connection 'EAP0'
20180527124258 11[CFG] loaded certificate "C=CA, O=btzdomainje.com, CN=btzdomainje.com" from 'btzSERVER_CERT.pem'
20180527124258 11[CFG] id '%any' not confirmed by certificate, defaulting to 'C=CA, O=btzdomainje.com, CN=btzdomainje.com'
20180527124258 11[CFG] added configuration 'EAP0'
20180527124258 06[CFG] received stroke: add connection 'EAP1'
20180527124258 06[CFG] loaded certificate "C=CA, O=btzdomainje.com, CN=btzdomainje.com" from 'btzSERVER_CERT.pem'
20180527124258 06[CFG] id '%any' not confirmed by certificate, defaulting to 'C=CA, O=btzdomainje.com, CN=btzdomainje.com'
20180527124258 06[CFG] added configuration 'EAP1'
20180527125529 14[NET] received packet: from 78.XXX.XXX.XXX (Privát adat)[42519] to 192.168.1.250[500] (704 bytes)
20180527125529 14[ENC] parsed IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(REDIR_SUP) ]
20180527125529 14[IKE] 78.XXX.XXX.XXX (Privát adat) is initiating an IKE_SA
20180527125529 14[IKE] local host is behind NAT, sending keep alives
20180527125529 14[IKE] remote host is behind NAT
20180527125529 14[IKE] DH group ECP_256 inacceptable, requesting MODP_2048
20180527125529 14[ENC] generating IKE_SA_INIT response 0 [ N(INVAL_KE) ]
20180527125529 14[NET] sending packet: from 192.168.1.250[500] to 78.XXX.XXX.XXX (Privát adat)[42519] (38 bytes)
20180527125529 06[NET] received packet: from 78.XXX.XXX.XXX (Privát adat)[42519] to 192.168.1.250[500] (896 bytes)
20180527125529 06[ENC] parsed IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(REDIR_SUP) ]
20180527125529 06[IKE] 78.XXX.XXX.XXX (Privát adat) is initiating an IKE_SA
20180527125530 06[IKE] local host is behind NAT, sending keep alives
20180527125530 06[IKE] remote host is behind NAT
20180527125530 06[IKE] sending cert request for "C=CA, O=btzdomainje.com, CN=btzdomainje.com Root btzCA"
20180527125530 06[ENC] generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) CERTREQ N(HASH_ALG) N(MULT_AUTH) ]
20180527125530 06[NET] sending packet: from 192.168.1.250[500] to 78.XXX.XXX.XXX (Privát adat)[42519] (481 bytes)
20180527125530 11[NET] received packet: from 78.XXX.XXX.XXX (Privát adat)[33004] to 192.168.1.250[4500] (2044 bytes)
20180527125530 11[ENC] parsed IKE_AUTH request 1 [ IDi CERT N(INIT_CONTACT) CERTREQ AUTH CPRQ(ADDR ADDR6 DNS DNS6) N(ESP_TFC_PAD_N) SA TSi TSr N(MOBIKE_SUP) N(NO_ADD_ADDR) N(MULT_AUTH) N(EAP_ONLY) N(MSG_ID_SYN_SUP) N(AUTH_FOLLOWS) ]
20180527125530 11[IKE] received cert request for "C=CA, O=btzdomainje.com, CN=btzdomainje.com Root btzCA"
20180527125530 11[IKE] received end entity cert "C=CA, O=btzdomainje.com, CN=CLIENT@btzdomainje.com"
20180527125530 11[CFG] looking for peer configs matching 192.168.1.250[%any]...78.XXX.XXX.XXX (Privát adat)[C=CA, O=btzdomainje.com, CN=CLIENT@btzdomainje.com]
20180527125530 11[CFG] selected peer config 'BASE'
20180527125530 11[CFG] using certificate "C=CA, O=btzdomainje.com, CN=CLIENT@btzdomainje.com"
20180527125530 11[CFG] using trusted ca certificate "C=CA, O=btzdomainje.com, CN=btzdomainje.com Root btzCA"
20180527125530 11[CFG] checking certificate status of "C=CA, O=btzdomainje.com, CN=CLIENT@btzdomainje.com"
20180527125530 11[CFG] certificate status is not available
20180527125530 11[CFG] reached self-signed root ca with a path length of 0
20180527125531 11[IKE] authentication of 'C=CA, O=btzdomainje.com, CN=CLIENT@btzdomainje.com' with RSA_EMSA_PKCS1_SHA256 successful
20180527125531 11[IKE] received ESP_TFC_PADDING_NOT_SUPPORTED, not using ESPv3 TFC padding
20180527125531 11[IKE] peer supports MOBIKE
20180527125531 11[IKE] authentication of 'C=CA, O=btzdomainje.com, CN=btzdomainje.com' (myself) with RSA_EMSA_PKCS1_SHA256 successful
20180527125531 11[IKE] sending end entity cert "C=CA, O=btzdomainje.com, CN=btzdomainje.com"
20180527125531 11[ENC] generating IKE_AUTH response 1 [ IDr CERT AUTH ]
20180527125531 11[NET] sending packet: from 192.168.1.250[4500] to 78.XXX.XXX.XXX (Privát adat)[33004] (1580 bytes)
20180527125531 05[NET] received packet: from 78.XXX.XXX.XXX (Privát adat)[33004] to 192.168.1.250[4500] (76 bytes)
20180527125531 05[ENC] parsed IKE_AUTH request 2 [ IDi ]
20180527125531 05[IKE] peer requested EAP, config inacceptable
20180527125531 05[CFG] switching to peer config 'EAP0'
20180527125531 05[CFG] constraint check failed: EAP identity '%any' required
20180527125531 05[CFG] selected peer config 'EAP0' inacceptable: non-matching authentication done
20180527125531 05[CFG] switching to peer config 'EAP1'
20180527125531 05[IKE] initiating EAP_IDENTITY method (id 0x00)
20180527125531 05[ENC] generating IKE_AUTH response 2 [ EAP/REQ/ID ]
20180527125531 05[NET] sending packet: from 192.168.1.250[4500] to 78.XXX.XXX.XXX (Privát adat)[33004] (76 bytes)
20180527125531 04[NET] received packet: from 78.XXX.XXX.XXX (Privát adat)[33004] to 192.168.1.250[4500] (76 bytes)
20180527125531 04[ENC] parsed IKE_AUTH request 3 [ EAP/RES/ID ]
20180527125531 04[IKE] received EAP identity 'btz'
20180527125531 04[IKE] initiating EAP_MD5 method (id 0xCA)
20180527125531 04[ENC] generating IKE_AUTH response 3 [ EAP/REQ/MD5 ]
20180527125531 04[NET] sending packet: from 192.168.1.250[4500] to 78.XXX.XXX.XXX (Privát adat)[33004] (92 bytes)
20180527125531 03[NET] received packet: from 78.XXX.XXX.XXX (Privát adat)[33004] to 192.168.1.250[4500] (92 bytes)
20180527125531 03[ENC] parsed IKE_AUTH request 4 [ EAP/RES/MD5 ]
20180527125531 03[IKE] EAP method EAP_MD5 succeeded, no MSK established
20180527125531 03[ENC] generating IKE_AUTH response 4 [ EAP/SUCC ]
20180527125531 03[NET] sending packet: from 192.168.1.250[4500] to 78.XXX.XXX.XXX (Privát adat)[33004] (76 bytes)
20180527125531 02[NET] received packet: from 78.XXX.XXX.XXX (Privát adat)[33004] to 192.168.1.250[4500] (92 bytes)
20180527125531 02[ENC] parsed IKE_AUTH request 5 [ AUTH ]
20180527125531 02[IKE] authentication of 'btz' with EAP successful
Várom az ötleteket, hogyan működhetne úgy a rendszer, hogy a DHCP szerver továbbra is a TP-Link marad, az IPSEC pedig továbbra is a DHCP-vel működik, tehát a rightsourceip=%dhcp beállításal.
ⓑⓣⓩ










 ekkold
ekkold